Telefónica suffers a ransomware attack
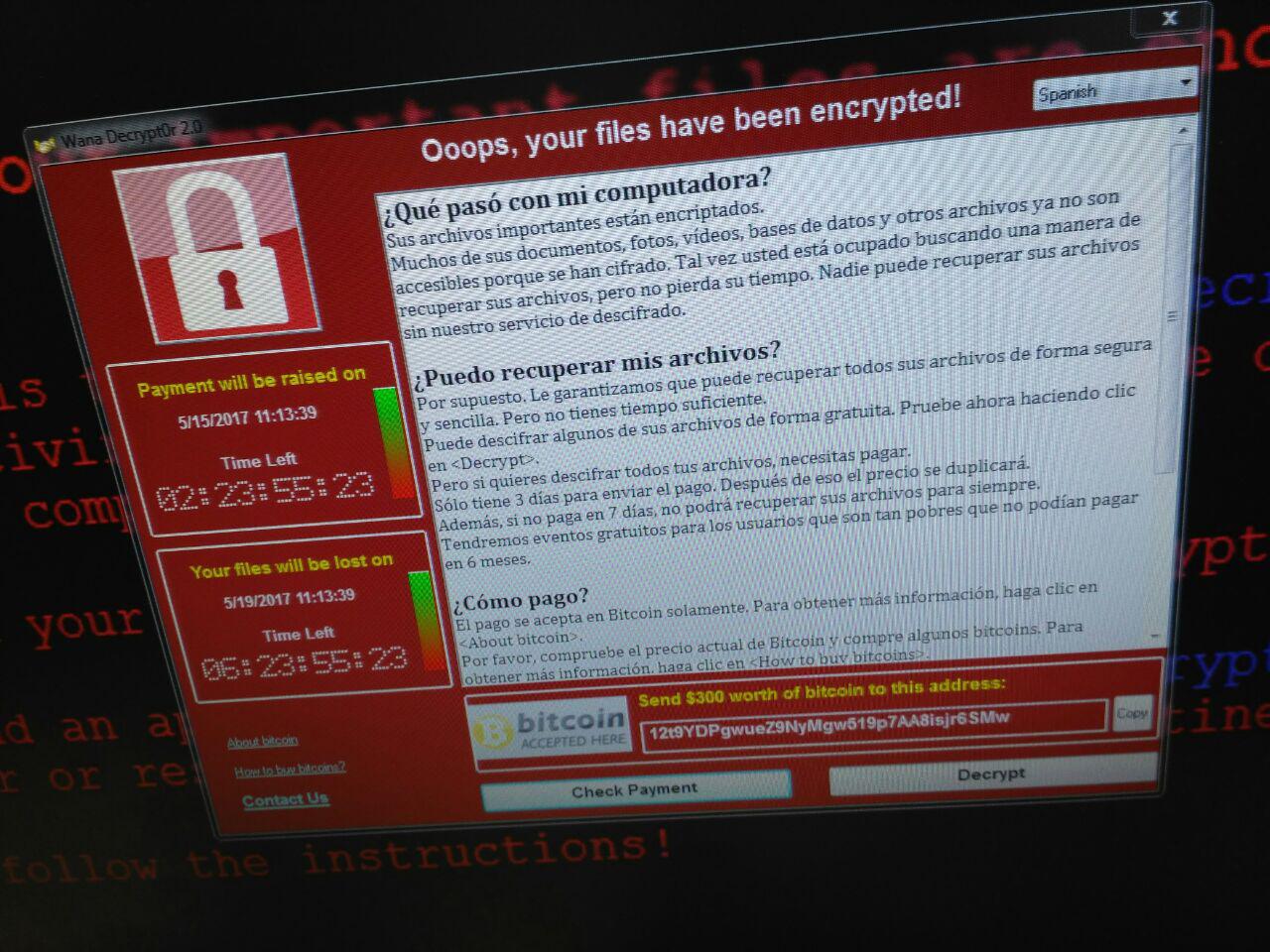
Table of contents:
Today we learn of a fairly significant attack on the internal Telefónica network that internal sources in the company confirm to us. This attack could also be affecting Vodafone, Santander and Capgemini. Telefonica was telling its employees over the public address system to turn off their computers to prevent the Ransomware from spreading throughout their network.
Telefónica suffers a Ransomware attack
It is not known exactly what is happening, but Telefónica has raised the alarm to its employees and some employees or staff are leaking information about what happened on social networks. We know that it is a fairly serious attack on the operator's internal network since they disconnected the equipment from the network and turned them off, in addition they gave the alert voice to the Datacenters that use their network so that they are aware.
Initially, the problem only affects Telefónica Spain and not only the headquarters but also the subsidiaries.

WanaDecryptor V2 is the name of the ransomware that is affecting Telefónica and other companies. WanaDecrypor uses remote command execution by taking advantage of the vulnerability of the SMB protocol that causes the malware to be distributed to the other Windows machines on that network.
The affected systems are Windows in different versions such as Windows Server 2008/2012/2016, Windows 7, Windows 8, Windows 8.1, Windows 10, Windows Vista SP2. According to that report, the vulnerability exploited in the cyber attack was included in a Microsoft security bulletin on March 14, and there is a support document to solve the problem that you can see here.

What you see in this photo is the statement that I released by phone to its employees to prevent the ransomware from spreading further. We have found several analyzes of this Malware in Hybrid Analysis and Total Virus.
Where is WanaDecryptor V2 installed?
Start by modifying the files for these paths:
C: \ WINDOWS \ system32 \ msctfime.ime
C: \ WINDOWS \ win.ini
C: \ DOCUME ~ 1 \ User \ LOCALS ~ 1 \ Temp \ c.wnry
C: \
C: \ DOCUME ~ 1 \ User \ LOCALS ~ 1 \ Temp \ msg \ m_English.wnry
Modify or add the following keys to the records:
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows NT \ CurrentVersion \ IMM
HKEY_USERS \ S-1-5-21-1547161642-507921405-839522115-1004 \ Software \ Microsoft \ Windows NT \ CurrentVersion \ AppCompatFlags \ Layers
HKEY_CURRENT_USER \ SOFTWARE \ Microsoft \ CTF
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ CTF \ SystemShared
HKEY_USERS \ S-1-5-21-1547161642-507921405-839522115-1004
HKEY_LOCAL_MACHINE \ Software \ WanaCrypt0r
HKEY_CURRENT_USER \ Software \ WanaCrypt0r
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows NT \ CurrentVersion \ ProfileList \ S-1-5-21-1547161642-507921405-839522115-1004
HKEY_LOCAL_MACHINE \ System \ CurrentControlSet \ Control \ Session Manager
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows NT \ currentVersion \ Time Zones \ W. Europe Standard Time
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows NT \ CurrentVersion \ Time Zones \ W. Europe Standard Time \ Dynamic DST
HKEY_CURRENT_USER \ SOFTWARE \ Microsoft \ CTF \ LangBarAddIn \
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ CTF \ LangBarAddIn \
More information on Malwr
Researcher stops ransomware attack with domain registration

An investigator stops the ransomware attack with a domain registration. Find out how this researcher stops WannaCry ransomware.
Formula 1 prevents a ransomware attack

Formula 1 prevents a ransomware attack. Find out how Formula 1 has managed to avoid becoming the victim of a ransomware attack.
Badrabbit: ransomware attack spreads across europe

BadRabbit: The ransomware attack is spreading across Europe. Find out more about this ransomware that affects companies in Russia and Ukraine.




